#57 - Tornado Cash and the Limits of Money Transmission
Scrutinizing Section 1960’s Reach: Non-Custodial Privacy Protocols and the DOJ’s Tornado Cash Case

Disclaimers and Thanks in Footnotes12
Stanford Blockchain Review
Volume 6, Article No. 7
Author: By Jacob E. Hirshman, Matt McGuire, and Kaili Wang
🌟 Technical Prerequisite: Advanced
In August 2023, the U.S. Attorney’s Office for the Southern District of New York filed sealed indictments against Roman Storm and Roman Semenov. The government alleges that Storm and Semenov created, operated, and promoted Tornado Cash3, which is an immutable set of smart contracts deployed to the Ethereum blockchain that allow users to anonymize the source of their transactions onchain without giving custody or control of their tokens to anyone else. Like other recent cryptocurrency prosecutions4, prosecutors charged Storm and Semenov with “knowingly conduct[ing], control[ling], manag[ing], supervis[ing], direct[ing], or own[ing]” an “unlicensed money transmitting business” under 18 U.S.C. § 1960, among other statutes.
Section 1960 was enacted in 1992 and, as the contemporaneous Senate Report shows, was part of the “War on Drugs” legislation passed in the early-to-mid 1990s. 5Today, Section 1960 is the basis for numerous financial crime prosecutions, stretching far beyond the sending of US dollars to overseas drug cartels to all manner of illicit financial transactions, whether involving currency like the US dollar or some other medium of exchange.6Through the Tornado Cash prosecutions, the government seeks to define a whole new class of “money transmitting” entities: developers of a decentralized protocol offering privacy for digital token transfers where no intermediary ever has control over the user’s tokens at any stage. The government’s theory is that Tornado Cash falls within Section 1960(b)(2) because the smart contracts are “transferring funds on behalf of the public by any and all means including but not limited to transfers within this country or to locations abroad by wire, check, draft, facsimile, or courier.”7
This paper advances a pair of related arguments against the interpretation (and expansion) of Section 1960(b)(2) advanced by the government in the Tornado Cash prosecution.
First, we look to the Supreme Court, which has never weighed in on how to interpret Section 1960. The Court, however, has been explicit (repeatedly) about how to interpret federal criminal statutes: give these statutes their ordinary meaning, but broad, ambiguous definitional terms cannot be construed to their maximum possible breadth in new contexts. Recent Supreme Court decisions make this clear. As the Court put it just last Term in Fischer v. United States: “We have long recognized that the power of punishment is vested in the legislative, not in the judicial department, and we have as a result traditionally exercised restraint in assessing the reach of a federal criminal statute.”8Consistent with Fischer and similar criminal statutory interpretation cases, the government’s sweeping and novel construction of Section 1960(b)(2) is immediately suspect.
Second, against that interpretive background, we assess the Financial Crimes Enforcement Network (“FinCEN”) guidance related to the scope of Section 1960(b)(2). Although this interpretive guidance does not carry the force of law on its own,9 it is indicative of the proper scope of federal statutory authority where the agency has proffered an interpretation, bounded by a limiting principle, that accords with the statute’s ordinary meaning. All told, FinCEN had it right when focusing on “control” and its applicability to Section 1960.
We begin with background on Tornado Cash to properly contextualize the government’s interpretation of Section 1960(b)(2).
I. Relevant Factual Background & Recent Legal Developments
A. What is FinCEN?
FinCEN is a bureau of the U.S. Department of the Treasury tasked with safeguarding the financial system from illicit activities, including money laundering and terrorist financing. Established by statutory mandate, FinCEN is responsible for administering the Bank Secrecy Act (“BSA”) and enforcing its provisions to detect, deter, and disrupt financial crimes.10
FinCEN’s core mission centers on promoting national security through the collection, analysis, and dissemination of financial intelligence.11By partnering with financial institutions, law enforcement, and international counterparts, FinCEN provides critical insights into illicit financial networks, enabling more effective detection and prosecution of criminal enterprises.12
The importance of FinCEN's work cannot be overstated. Money laundering undermines the integrity of financial systems, facilitates organized crime, and jeopardizes the stability of economies. By enforcing anti-money laundering (“AML”) policies, FinCEN protects the U.S. financial system from abuse, supports the prosecution of financial criminals, and advances the United States' broader national security and economic stability objectives. Its efforts are essential to ensuring that the financial system remains a trusted and transparent foundation for legitimate economic activity. FinCEN is best positioned as the regulator able to assess, and encourage reliance on, new methods like blockchain analytics, which can identify transactions that may be higher risk or impermissible.13 Leveraging new, blockchain-native tools is one way to respond to risks in the broader ecosystem, and there will assuredly be additional innovations over time that identify and stop high-risk activity without compromising a user’s privacy.
As will be discussed in further detail below, FinCEN has published two pieces of interpretive guidance on the digital asset markets “to remind persons subject to the Bank Secrecy Act (BSA) how FinCEN regulations relating to money services businesses (MSBs) apply to certain business models involving money transmission denominated in value that substitutes for currency, specifically, convertible virtual currencies (CVCs).”14Because of the importance of FinCEN’s mission and the lack of additional legislative or rulemaking activity from the government related to the application of the BSA to digital asset markets, market participants have relied heavily on this interpretive guidance to structure their product offerings in a manner which complies with the nation’s AML laws.15
B. Description of Tornado Cash
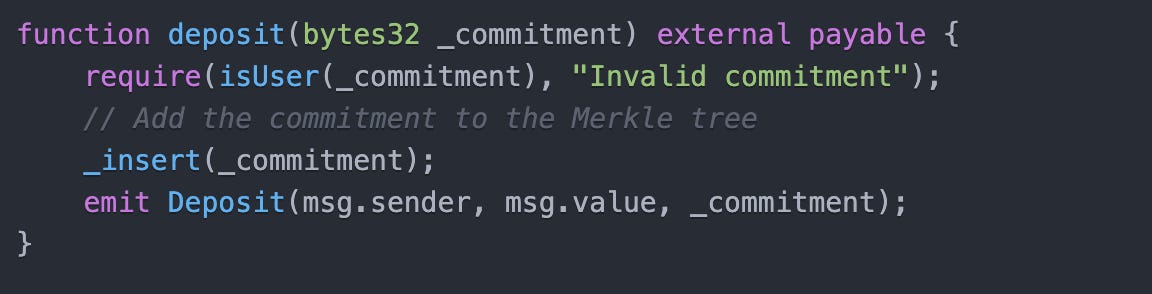
Tornado Cash is a decentralized, non-custodial privacy solution built on the Ethereum blockchain. It allows users to enhance the privacy of their cryptocurrency transactions by breaking the onchain link between the source and destination addresses. The Tornado Cash protocol operates by allowing multiple users’ to lock their tokens in the same smart contract, and then allowing a user to unlock their tokens to a different cryptocurrency wallet address than the one used when locking tokens into the smart contract. It is the user’s ability to use different wallets for locking and unlocking that makes it difficult to trace individual transactions. But it is always clear that a user interacted with the Tornado Cash smart contracts — blockchain analytics can identify that a wallet locked tokens, and that a wallet unlocked tokens, so the use of Tornado Cash itself is not private.
How Tornado Cash Works
Locking Tokens16:
A user generates a unique cryptographic note (a secret) and locks a certain amount of Ethereum (ETH) or ERC-20 tokens17 into the Tornado Cash smart contract. The secret note is also used to generate the nullifier, which will later be used to ensure that each deposited amount is unlocked only once.18
This locking action records a commitment19 to the blockchain without linking it to the address later used to unlock the funds.
The user must save the secret note themselves, usually on their device. If they fail to do so, then their funds will be permanently blocked from unlocking.
Anonymity Set:
Multiple users lock tokens into the same smart contract address, effectively creating an anonymity set of multiple users locking similar ledger amounts in fixed amounts (e.g., 1 ETH, 10 ETH, or 100 ETH). This means that when fixed amounts of tokens are unlocked, it is not readily apparent which user corresponds to which of the value amounts. The more users locking the same fixed amounts in the same smart contract, the greater the level of anonymity.
Unlocking Tokens:
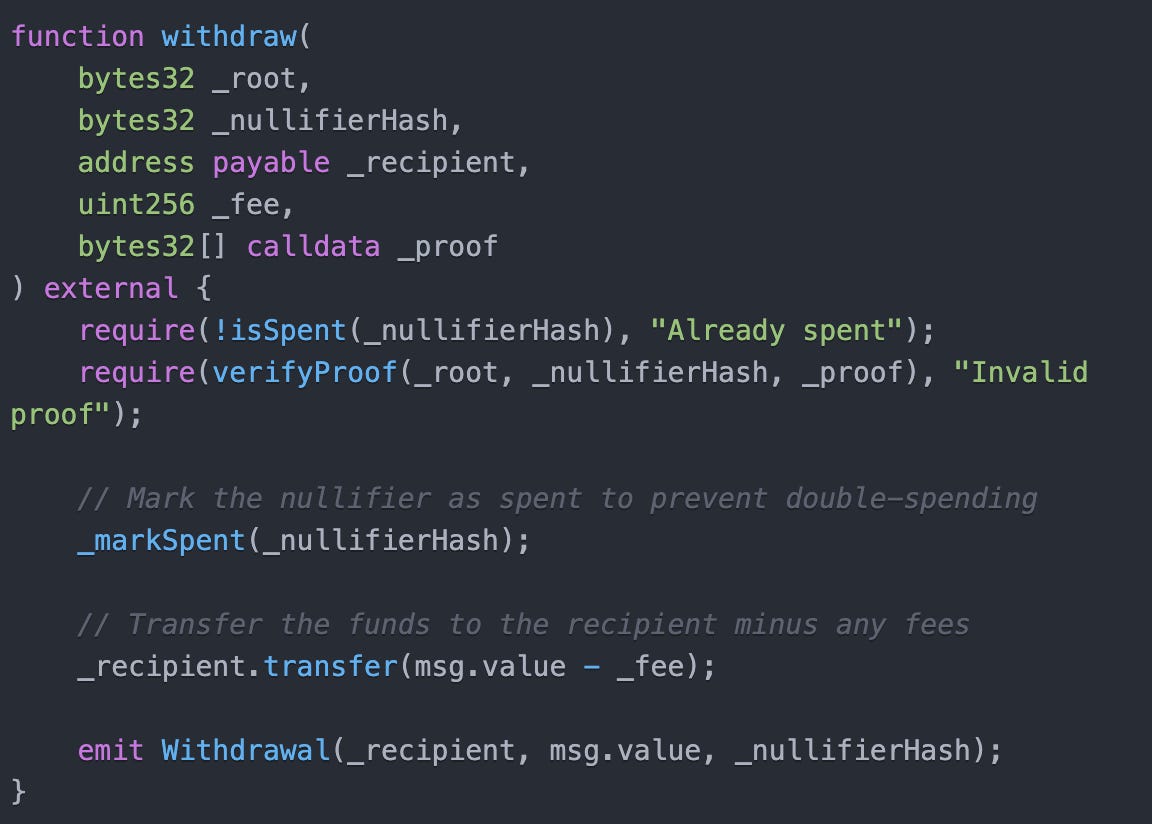
To unlock, the user uses their unique proof (derived from the secret note) to claim their tokens from the smart contract that they originally deposited tokens in. The cryptographic proof proves that the user has a record of the secret note, without revealing what the secret note actually is. The proof also reveals the nullifier to prove that the token was not claimed before. The contract will record all used nullifiers.20
The unlocking address should be different from the locking address, providing the user privacy on an otherwise immutable, public ledger.
Unlike a bank or centralized exchange, the protocol is non-custodial, meaning no third party ever has control over users' tokens at any point. Users retain full ownership and responsibility for their assets throughout the process—if a user loses their cryptographic note, then their tokens are permanently locked in the Tornado Cash immutable smart contracts and no third party has the ability to otherwise release those tokens. In a sense, non-custodial solutions like Tornado Cash are the onchain equivalent of keeping gold bars under a mattress, and there is no recourse to retrieve any lost tokens.
Key Smart Contract Features Demonstrating Non-Custodial Operation
It is helpful to go a bit deeper on how the Tornado Cash protocol is non-custodial, because the smart contracts are specifically designed to ensure that no third party, including the developers, has the authority to access or control a user’s tokens. Below are key aspects of the smart contract code that support this:
Locking Function (lock tokens):
Explanation: This code reference allows users to lock tokens by providing a commitment. The contract merely stores the commitment without tying it to the user's address.
Unlocking Function (unlocking tokens):
Users submit a proof that they possess the secret note and nullifier corresponding to a prior token lock.
The contract verifies the proof against the stored Merkle tree without needing to know the locking entity's identity.
Here is the specific code reference accomplishing the unlock:
Explanation: The unlocking function allows users to retrieve their tokens by proving ownership (of the secret note) without revealing any link to the locking wallet address. The contract ensures that tokens are only transferred to the specified recipient if the the nullifier and proof are valid, without any other party having access to manage or redirect tokens. It is possible for a user to lose the secret note, in which case the tokens are not recoverable.
Merkle Tree Management:
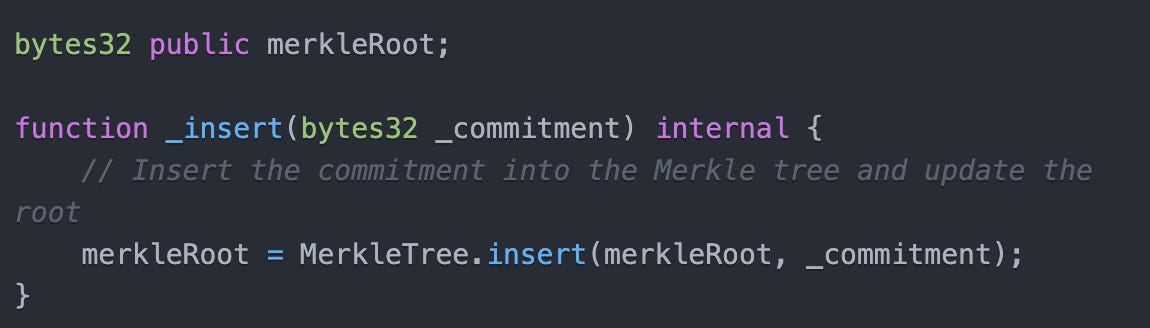
The smart contract maintains a Merkle tree of all commitments.23
Here is the specific code reference accomplishing the Merkle tree:
Explanation: Managing the Merkle tree internally ensures that the contract only tracks commitments, not actual user identities or token balances, reinforcing non-custodial principles.
No Administrative Controls:
The smart contracts do not include functions that allow administrators to unlock tokens or alter balances.24
Explanation: Without administrative functions, there is no entity with the authority to control user tokens, ensuring that the protocol remains non-custodial.
How Tornado Cash Ensures Exact Unlock Amounts
Ensuring that the tokens unlocked from the Tornado Cash smart contracts are unlocked in the exact same amounts as those originally locked is fundamental to the operation of the service. This exactness is achieved through the smart contracts’ design, which enforces strict rules around these amounts.
Fixed Denominations:
The protocol operates by allowing locked amounts in predefined, fixed denominations (e.g., 1 ETH, 10 ETH). This standardization ensures that each token lock corresponds to a specific unlock amount.
Commitment to Specific Amounts:
When a user locks tokens, they generate a cryptographic commitment for that amount. This commitment is recorded in the smart contract's Merkle tree, linking it to the user’s secret note without revealing their identity.
Proof Verification:
During the unlocking process, the user must provide a zero-knowledge proof that verifies they possess the secret note. This proof ensures that the unlock links to both the commitment (another user-generated value linked to the secret note) and to an unspent locked amount, without exposing any additional information. The user also provides a nullifier derived from the secret note.
Smart Contract Constraints:
The smart contracts ensure that unlocks can only be made for the exact denominations specified when locking tokens. Any attempt to unlock a different amount will result in the transaction being rejected.
Tornado Cash's smart contract architecture verifies that the amount of tokens unlocked are identical to those that were locked. Through fixed denominations, commitment validation, and strict proof verification, the smart contract architecture ensures that users can reliably lock and unlock exact amounts without any discrepancies. This exactness upholds the protocol’s integrity and further demonstrates that Tornado Cash is non-custodial.
C. Recent Legal Developments related to Tornado Cash
The U.S. Court of Appeals for the Fifth Circuit recently confirmed the non-custodial nature of Tornado Cash in a case interpreting the statutory text of the International Emergency Economic Powers Act. In Van Loon v. Department of the Treasury, the Court considered whether the protocol’s “immutable smart contracts (the lines of privacy-enabling software code)” are “‘property’ of a foreign national or entity.”25 As the Court explained, the relevant “smart contracts became self-executing and could no longer be altered, removed, or controlled” after the developers’ “trusted setup ceremony.”26 Likewise, the Court described how a user alone remains in control of their tokens whenever they interact with the protocol, and that description is worth quoting at length:
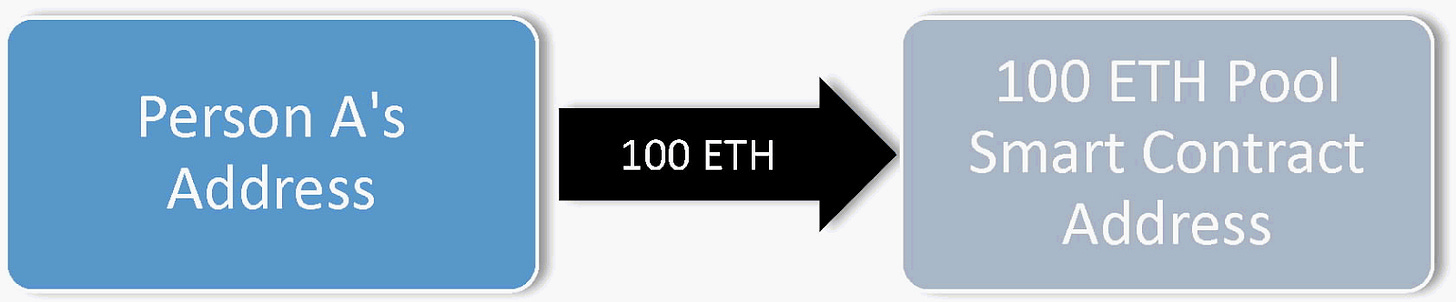
For example, someone who wants to deposit and withdraw 100 Ether would start by sending 100 ETH to the “100 ETH Pool Contract.” That transaction would look something like this:
Depositors then receive keys or a password entitling the holder to withdraw the same amount from a given pool, and this withdrawal can be made to an entirely different wallet than the depositing wallet, thus “sever[ing]” “any public link between the deposit and withdrawal addresses.” The software code that forms the pool smart contract will trigger a withdrawal from the pool only after it verifies the password. So when the person goes to withdraw the amount to a second address, the second transaction would look something like this:
And critically, the Court confirmed that “the entire process occurs automatically—with no human intervention.”28
Based on those facts, the Court held that “[t]he immutable smart contracts at issue in th[e] appeal are not property because they are not capable of being owned.”29 The Court also rejected the argument that the immutable smart contracts were legal “contracts” because there is “only one party in play”: the user.30 The immutable smart contracts allow “[a] third-party user [to] make an offer, but there is no smart-contract operator on the other side of the transaction to accept or make a counteroffer.”31 It is “just software code,” and “[b]ecause no one can control immutable smart contracts (or the Ether deposited in the pools), there is no party with which to contract.”32
D. What is at Risk? Understanding the Threat of Prosecutorial Overreach and Legislation from the Bench
The DOJ’s aggressive application of 18 U.S.C. § 1960 in this case raises questions that extend far beyond the immediate context of blockchain technologies. At its core, this prosecution exemplifies the dangers of allowing unelected officials to stretch statutory language to address novel challenges, inviting the judiciary to act beyond their constitutional authority and usurp the power of congress by legislating from the bench. Such an approach bypasses the democratic process, undermining the constitutional framework that vests legislative authority in Congress and enforcement discretion in the executive.
The DOJ’s interpretation of Section 1960 is emblematic of a broader trend in which prosecutors leverage anachronistic interpretations of statutes written before widespread adoption of the internet and the invention of blockchains to address contemporary issues (as discussed in greater detail in Section II below). This practice has significant implications for the global perception of U.S. legal and economic systems. The potential criminalization of software developers based on an unprecedentedly broad reading of a criminal statute, represents a threat to the U.S. position as the innovation hub of the world. This approach could discourage the brightest minds across the globe from engaging with U.S.-based technologies or collaborating with American developers, weakening the nation’s competitive edge in emerging fields like blockchain and artificial intelligence. At a time when our adversaries seek to usurp our economic position for their own gain, the stakes could not be higher.
The DOJ’s stance also risks undermining the delicate balance between privacy and regulation in the digital age. Tornado Cash’s non-custodial design reflects a broader societal demand for privacy-preserving financial tools. Criminalizing the development of such tools conflates technology with its misuse, a dangerous precedent with parallels in historical debates over encryption technologies like Pretty Good Privacy (“PGP”) encryption.33
The need for the development of strong privacy tools, both in the financial services industry and in the communications industry, is highlighted by a recent statement from high-ranking U.S. officials warning American citizens to use encrypted messaging applications because of a significant risk of cyber attack by the Chinese government.34 Rather than prosecuting innovation, policymakers should focus on creating clear, forward-looking regulations that address illicit activity without stifling legitimate use cases or discouraging technical progress.
The absurdity of the potential outcome here is not limited to just privacy and innovation. The affirmation of the DOJ’s position in court would also threaten the incredible strides that the country’s digital infrastructure has made over the last three decades. There are a broad range of technology service providers that are involved with the value chain that facilitate the movement of money that we have come to take for granted in this country. While the immediate focus of this paper is on blockchains, there are significant potential implications for fintech more broadly, and even generalized software and hardware providers. Every time a consumer pays for goods on their phone, there are non-custodial software and hardware providers that have zero control over the money involved that are necessary to complete that transaction. The DOJ’s broad construction of Section 1960 could sweep in all of these services, which is not what Congress intended and would have the perverse impact of decreasing the safety, efficiency, and effectiveness of our markets.
By pushing back against prosecutorial overreach, the DOJ or the judiciary have the opportunity to encourage Congress to legislate with clarity, ensuring that legal frameworks for emerging technologies are shaped through open debate rather than judicial interpretation.35
II. Federal Courts Must Exercise Restraint When Assessing the Reach of Ambiguous Federal Criminal Statutes
As Van Loon shows, federal statutes are given their ordinary meaning and are not construed to cover “blind spots or smooth[] disruptive effects” caused by new technologies.36 So, although the scope of Section 1960(b)(2) has not been directly addressed by the Supreme Court or courts of appeals, that does not mean the government or the courts are writing on a blank slate. Numerous cases have been decided over the past 20 years that call into question the extreme breadth of the government’s position related to section 1960 and the Tornado Cash developers. Whether one calls it lenity, fair notice, constitutional avoidance, or federalism, the Supreme Court has been consistent and clear: if there is reasonable doubt about whether the statute covers the conduct, courts should exercise restraint and defer to Congress.37
Recent Supreme Court precedent on this point has been overwhelmingly consistent across various, unrelated federal criminal laws. In cases like Fischer, Snyder v. United States,38 Dubin v. United States,39 Marinello v. United States,40 and McDonnell v. United States,41 the Court pointed out the “staggering breadth” of the government’s arguments when interpreting the various criminal statutes.42 And in each case, the Court rejected the government’s interpretation:
Fischer: interpreting two provisions of Sarbanes-Oxley Act of 2002, 18 U.S.C. § 1512(c)(1) and (c)(2), and whether the “otherwise” clause of (c)(2) extends the criminal liability established in (c)(1).43 When interpreting “the residual clause,” the Court assessed the “surrounding words” as well as the “specific context” around the clause “and the broader context of the statute as a whole.”44 In rejecting the government’s interpretation, the Court noted that the “all-encompassing interpretation may be literally permissible” but “it defies the most plausible understanding” of the statutory construction and “is inconsistent with the context from which the statute arose.”45 Indeed, the Court pointed out that the provision “was enacted to address the Enron disaster, not some far flung set of dangers,” and “it is unlikely that Congress responded with such an unfocused and ‘grossly incommensurate patch.’”46
Snyder: construing 18 U.S.C. § 666 as it relates to acceptance of gratuities or tokens of appreciation by state and local officials.47 After evaluating six separate reasons (text, history, structure, punishments, federalism, and fair notice), the Court rejected the government’s interpretation, under which either (a) the government could “ban all gratuities, no matter how trivial, in connection with covered official acts”; or (b) the government “could recognize the irrationality of reading [the statute] to criminalize all such gratuities” and “could make up atextual exceptions on the fly.”48 The government had chosen option (b), but it “offer[ed] no clear federal rules for state and local officials.”49 According to the Court, the “federal criminal law” does not permit the government to “leave state and local officials entirely at sea to guess about what gifts they are allowed to accept under federal law, with the threat of up to 10 years in federal prison if they happen to guess wrong.”50
Dubin: interpreting 18 U.S.C. § 1028A(a)(1) and the meaning of “aggravated identity theft” where the defendant submitted an inflated reimbursement to Medicaid with the patient’s name on it.51 The statute addresses “using a patient’s means of identification in relation to healthcare fraud,” and the government proffered an interpretation reading the various terms “broadly and in isolation.”52 After considering the text and context (including the statute’s title), the Court noted the “staggering breadth of the [g]overnment’s reading,” and explained that “[t]ime and again, this Court has prudently avoided reading incongruous breadth into opaque language in criminal statutes.”53 The Court adopted the narrower interpretation with a clear eye to “the far-reaching consequences of the Government’s reading”, which “underscored the implausibility of” that construction.54
Van Buren: interpreting the Computer Fraud and Abuse Act of 1989, “which makes it illegal to ‘access a computer with authorization and to use such access to obtain or alter information in the computer that the accesser is not entitled so to obtain or alter.”55 The defendant had used his police computer access to look-up a fake license plate for a civilian as part of an FBI undercover operation.56 The Court readily concluded that the “statute’s language spells trouble for the [g]overnment’s position,” and further noted that “a wider look at the statute’s structure gives [the Court] even more reason for pause.”57 Stepping even further back, the Court concluded that “the [g]overnment’s interpretation of the statute would attach criminal penalties to a breathtaking amount of commonplace computer activity.”58
Marinello: construing 26 U.S.C. § 7212(a), which “makes it a felony ‘corruptly or by force’ to ‘endeavor to obstruct or impede the due administration of this title.’”59 After evaluating the statutory text, context, and legislative history, the Court rejected the government’s construction that would have applied the criminal statute to “virtually all governmental efforts to collect taxes.”60 In support of the narrower construction, the Court also observed that “insofar as the public fears arbitrary prosecution, it risks undermining necessary confidence in the criminal justice system.”61
McDonnell: construing the meaning of “official act” in 18 U.S.C. § 201(a)(3) as it relates to bribery. The government argued that “Congress used intentionally broad language” in the statute “to embrace any decision or action, on any question or matter, that may at any time be pending, or which may by law be brought before any public official, in such official’s official capacity”—which “encompasses nearly any activity by a public official.”62 The Court looked to dictionaries, statutory context, and related canons of interpretation and “adopt[ed] a more bounded of interpretation of ‘official act.’”63 Despite the permissibility of the government’s interpretation, the Court rejected “the standardless sweep of the [g]overnment’s reading.”64
Prosecutorial discretion is no justification or safe haven for broad interpretations of federal criminal statutes or disregard for the rule of law. In most of these cases, the government made “a familiar plea: [t]here is no reason to mistrust its sweeping reading, because prosecutors will act responsibly.”65 Dubin, McDonnell, and Marinello all hold the same thing: criminal statutes cannot be construed “on the assumption that the [g]overnment will use it responsibly.”66 The extreme power of prosecutors was “particularly salient” in Dubin where prosecutors could “hold the threat of charging an additional 2-year mandatory prison sentence over the head of any defendant considering going to trial.”67
It is against this comprehensive and consistent federal criminal statutory interpretation background that the government’s expansive application of Section 1960 must be evaluated.
III. The Text and Context of Section 1960(b)(2) Makes Application to Tornado Cash Unclear
A. The Text and Context of Section 1960(b)(2) Shows that the Statute Does Not Apply to Tornado Cash, or at a Minimum, the Applicability is Uncertain
Section 1960, titled “Prohibition of unlicensed money transmitting businesses,” provides that:
Whoever knowingly conducts, controls, manages, supervises, directs, or owns all or part of an unlicensed money transmitting business, shall be fined in accordance with this title or imprisoned not more than 5 years, or both.68
And Section 1960(b)(2) defines “money transmitting”:
The term “money transmitting” includes transferring funds on behalf of the public by any and all means including but not limited to transfers within this country or to locations abroad by wire, check, draft, facsimile, or courier.
So, to find someone guilty of an offense under Section 1960, the government must prove that the person was engaged in money transmission as that term is defined in subsection (b)(2).
As in every case, the starting point is the text of the statute.69 Here, we are focusing on the key word “funds” as well as the phrase “by any and all means” and its explanatory clause and list of transfer mechanisms: “wire, check, draft, facsimile, or courier.” Starting with “funds,” dictionaries indicate that funds used in connection with a transfer or transaction typically refers to money:
Black’s Law Dictionary:70
“Fund”: “A sum of money or other liquid assets established for a specific purpose. . . . Money or other assets, such as stocks, bonds, or working capital, available to pay debts, expenses, and the like.”
“Funds Transfer”: “A payment of money from one person or entity to another; esp., the process by which payment is made through a series of transactions between computerized banking systems, beginning with an originator’s payment order and ending when a final payment order is received by the beneficiary’s bank.”
Merriam Webster:71
Comparing legal definitions with lay definitions yields a consistent theme in terms of how “fund” is understood with reference to transfers. “Fund” is mostly a reference to money available to a person or entity that is readily usable to make payments for various purposes. That definition aligns with the legislative history of Section 1960, which points to concerns with drug money payments and payments to terrorists.74
The specific transfer mechanisms identified in statute likewise have common elements:
“Wire”:
“A transfer of funds (as from one bank account to another) by electronic or formerly by telegraphic means.”75
“Check”:
“Draft”:
“An unconditional written order signed by one person (the drawer) directing another person (the drawee or payor) to pay a certain sum of money on demand or at a definite time to a third person (the payee) or to bearer. A check is the most common example of a draft.”78
“An order for payment of money drawn by . . . one person or bank on another.”79
“Facsimile”:
“Courier”:
The first three terms (wire, check, and draft) are all different payment instruments where, in each case, there is an intermediary (often a bank) that controls a third party’s funds and makes payments at their instruction. The last two terms (facsimile and courier) are alternative payment delivery methods for a payment instrument— a person sending funds using a check could send it via fax or courier as opposed to mailing it. As these enumerated traditional, intermediated financial transaction methods make clear, Congress was not considering non-custodial transactions, like the Tornado Cash protocol, when enacting or amending Section 1960.
Statutory context further confirms that a “money transmitter” is a person or entity that has control over a third party’s money or equivalent as part of the transfer process. A related money-services-business statute, 31 U.S.C. § 5330, is referenced in Section 196084 and imposes a registration requirement for a “money transmitting business.”85 In defining “money transmitting business,” Section 5330 confirms that there must be a “business” that is “own[ed] or control[led]” by a person,86 and that the “business” must be either (1) a “money transmitting service,” or (2) “engage[d] as a business in the transmission of currency, funds, or value that substitutes for currency.”87 The express statutory references to a “business” under a person’s control engaged in certain conduct aligns neatly with Section 1960’s enumerated financial transactions, which all contemplate an intermediary entity in control of someone’s funds and conducting the transaction on their behalf.
Section 5330’s definition of “money transmitting services” is consistent with that interpretation. Under the statute, “money transmitting services” is defined as “accepting currency, funds, or value that substitutes for currency and transmitting the currency, funds ,or value that substitutes for currency by any means, including . . . an electronic funds transfer network.” Even if a smart contract that allows a user to lock their tokens for future retrieval by themselves constitutes “accepting” by the smart contract, Section 5330 still requires there to be a business or person doing the “accepting.” Just like the enumerated financial transactions in Section 1960, Section 5330 looks for an entity or person in control of the “accepting” such that the entity or person is then capable of “transmitting” the relevant funds. Where a smart contract is “just software code” that is outside the control of a person or entity, there’s simply no “money transmitting business” under Section 5330.88
In sum, Section 5330 was enacted after Section 1960,89 and “identical words used in different parts of the same statute are . . . presumed to have the same meaning” unless “a material variation in terms suggests a variation in meaning.” 90Both Section 1960 and Section 5330 address a “money transmitting business,”91 “money transmitting,”92 and speak in terms of “funds”93—as the U.S. Supreme Court routinely explains, these provisions of the statutes are read in pari materia and should be construed “as if they were one law.”94 Section 1960 and Section 5330 thus presumptively have the same meaning when it comes to “money transmitting business” based on ordinary principles of statutory interpretation.95 Moreover, that interpretation also adheres to the canon that “provisions of a text should be interpreted in a way that renders them compatible, not contradictory,”96 and ensures a “symmetrical and coherent regulatory scheme.”97 Thus, absent a person or entity in control of the money transmission process, neither Section 1960 or Section 5330 apply.
B. FinCEN Guidance Correctly Links Liability Under Section 1960 to “Control”
In the criminal context, if there is reasonable doubt about whether a statute covers the alleged conduct, absent any other guidance, it is reasonable for market participants to rely on interpretive rules (or guidance documents).98 In the last twelve years, the government has provided precisely two pieces of interpretive guidance on how existing obligations under the BSA apply to digital asset market participants.99 The stated goal of this guidance is to facilitate compliance with the country’s AML laws. With respect to the Tornado Cash protocol, it is the latter of these two pieces of guidance, the 2019 FinCEN guidance (“2019 Guidance”), that is at issue and addresses the question of whether liability under Section 1960 is linked to a person or entity’s control of the underlying token. FinCEN’s statements in the 2019 Guidance and its enforcement history establish that, absent control of the underlying token, the developers of Tornado Cash cannot be found to be acting as an unlicensed money transmitting business.
At the outset, the 2019 Guidance states that it “does not establish any new regulatory expectations or requirements. Rather, it consolidates current FinCEN regulations, and related administrative rulings and guidance issued since 2011, and then applies these rules and interpretations to other common business models involving convertible virtual currency (“CVC”) engaging in the same underlying patterns of activity.”100 In the absence of additional legislative activity, rulemaking, or guidance with regard to the regulatory obligations of digital asset market participants under the BSA, the 2019 Guidance has been relied on by both the government and market participants alike to understand whether certain activity in these markets constitutes money transmission.101
The government’s allegations in Tornado Cash rightly state that “the FinCEN Guidance is not a regulation or rule,” however, the arguments outlined in the previous sections call into question the government’s position that the guidance “has no authoritative effect” in this case.102 But it is logical and expected for market participants engaged in the same underlying pattern of activity as discussed in the agency guidance to conduct their activity in line with such guidance, which is designed precisely to facilitate compliance with the law for market participants who may be regulated by the agency as well as participants that may be adhering to the guidance in case of future regulation. In their allegations, the DOJ wrongfully disregards this guidance as inapplicable in this case and instead seeks to interpret a criminal statute in the widest possible breadth.
1. The Previous Case Law on Privacy Applications Has Only Focused on Centralized, Custodial Mixing Services
As explained above, the case law about centralized mixers informs the government’s theory with respect to the Tornado Cash protocol, despite the obvious differences. In previous cases involving mixers, the government has advocated for a broad reading of both statutory definitions (under 18 U.S.C. § 1960 and 31 U.S.C. § 5330) and regulatory definitions (under 31 C.F.R. § 1010.100(ff)(5)) of money transmission to argue that the mixers were operating as unlicensed money transmitters.103 In Harmon, the DOJ claimed that the mixer’s transfer of funds from one location to another on the blockchain qualified as money transmission, and the mixer was therefore operating in violation of Section 1960(a).104 Arguments made by the DOJ in Sterlingov, where the defendant did not contest whether the centralized mixing service Bitcoin Fog was in fact a money transmitting business, also cited Harmon in asserting more generally that courts have had “few difficulties” broadening traditional statutes to apply them to virtual currency contexts despite their relative novelty in case law.105
Tornado Cash is readily distinguishable from the mixers at issue in previous crypto cases for the technical reasons previously described. To put it simply, unlike Bitcoin Fog, Tornado Cash is a decentralized protocol where no intermediary ever has control over a user’s tokens. Additionally, in Harmon, the parties’ arguments focused on whether bitcoin was indeed transferred from one location to another, rather than focusing on control, for money transmission: the court cited the 2019 Guidance to hold that centralized mixers could be money transmitters if the entity “‘uses’ the anonymized bitcoin in his possession ‘to accept and transmit value from one person to another person or location.’”106 Because no component or developer of Tornado Cash ever accepts or controls a user’s tokens, the tokens are not in their “possession” and the protocol does not qualify as money transmission.
2. Tornado Cash Should be Evaluated Under the CVC Wallet Section of the 2019 Guidance
a) CVC Wallet Section
In Section 4.2 of its 2019 Guidance (the “CVC Wallet Section”), FinCEN provided the following four-factor test for determining the BSA obligations of persons that act as intermediaries between the owner of CVC and the CVC itself.107 According to FinCEN, the regulatory treatment depends on four criteria: (i) who owns the value; (ii) where the value is stored; (iii) whether the owner interacts directly with the payment system where the CVC runs; and (iv) whether the person acting as intermediary has total independent control over the value (“Four-Factor Test”).
In the context of wallet software providers, FinCEN stated that if:
(i) the value belongs to the owner; (ii) the value is stored in a wallet or represented as an entry in the accounts of the provider; (iii) the owner of the value interacts with the provider and not the payment system; and (iv) the provider has total independent control over the value, the wallets are “hosted,” and the provider is likely a money transmitter. By contrast, if: (i) the value is owned by the owner; (ii) the value is stored in the wallet; (iii) the owner of the value interacts with the payment system directly; and (iv) the owner has total independent control over the value, the wallet is “unhosted,” and the provider is unlikely to be a money transmitter. According to FinCEN, “unhosted wallets do not require an additional third party to conduct transactions.”
In this section, FinCEN explicitly states that “the regulatory interpretation of the BSA obligations of persons that act as intermediaries between the owner of the value and the value itself is not technology dependent.”108 The government never analyzes the Tornado Cash protocol under this section, because according to the government, “the Tornado Cash service is not a wallet provider.”109
b) Providers of Anonymizing Services for CVC
Section 4.5.1 of the 2019 Guidance discusses "Providers of Anonymizing Services for Convertible Virtual Currencies (CVCs)" and differentiates between anonymizing service providers and anonymizing software providers.110 It describes two types of providers of anonymizing services, “anonymizing services providers” and “anonymizing software providers.”111
According to the 2019 Guidance, an “anonymizing service provider” is “a person (acting by itself, through employees or agent, or by using mechanical or software agencies) who provides anonymizing services by accepting value from a customer and transmitting the same or another type of value to the recipient, in a way designed to mask the identity of the transmittor.”112 They are classified as money transmitters under FinCEN regulations because, according to the agency, their activities constitute money transmission services, even if the transmission includes added features like source anonymization.113 Such providers must comply with the BSA obligations, including registration, recordkeeping, and reporting. This interpretation is aligned with the proper interpretation of Section 1960 and Section 5330 as there is an intermediary—the “service provider”—that obtains total independent control over the funds by accepting and transmitting the funds from the user.
An “anonymizing software provider” on the other hand is an entity that develops or distributes software enabling individuals to anonymize their own CVC transactions. Anonymizing software providers are not considered money transmitters because they merely supply tools (software, communication services, etc.) rather than actively engaging in the acceptance and transmission of value as a business. However, FinCEN notes that individuals or entities using such software can be classified as money transmitters if their activities involve transmitting value on behalf of others. Put differently, if a business accepted tokens from its users and then used the Tornado Cash protocol with its users’ tokens, that business, not the protocol, may be engaged in money transmission.
c) Tornado Cash Has Features of Both a CVC Wallet and a Provider of Anonymizing Services (an Anonymizing Software Provider)
Although it is true that the 2019 Guidance states that a provider of anonymizing services can be a money transmitter, it also makes clear that anonymizing software providers are not engaged in money transmission. To determine whether the Tornado Cash protocol is anonymizing software or an anonymizing service, we can look to other parts of the 2019 Guidance to inform our view of whether the activity is “trade and not money transmission.”114
Nothing in the 2019 Guidance indicates that simply because there is a section that may apply to a smart contract that helps users achieve privacy through pooling, that no other section in the 2019 Guidance also may apply to that service. Indeed, that position would be inconsistent with the sections addressed above—FinCEN properly recognized that there are different technological ways of achieving the same thing, and the regulations depend on how the technology works. As the FinCEN Guidance says explicitly: “[T]his guidance applies to any business model that fits the same key facts and circumstances described in the guidance, regardless of its label. Conversely, the regulatory interpretations in this guidance will not apply to a business model using the same label, but involving different key facts and circumstances.”115
DOJ baldly asserts that Tornado Cash (again, the government makes no distinction for the different components of Tornado Cash and elides the smart contracts with other components of Tornado Cash) is covered under the BSA as an anonymizing services provider and thus is a money transmitter. But the Guidance clearly states that finding that an anonymizing service provider is a money transmitter is predicated on finding that the service provider is engaged in “accepting value from a customer.”116 Indeed, looking at the history of enforcement actions against crypto-based privacy services, we see that, until recently, the enforcement history has only pursued actions against mixers that are custodial and with an entity or person that clearly “accepts” value from a customer.117 By requiring that there be a “person” (the service provider) “accepting” funds from a user, FinCEN, in this context, considered the definition of money transmission to require actual acceptance of CVC by the service provider. FinCEN thus was relying on the interpretation of Section 1960 articulated above,118 and was not relying on the broader definition of Section 1960(b)(2) as construed by DOJ.
The Tornado Cash protocol lacks a “service provider” that “accepts” funds from a user, which is why the “mixer” and “anonymizing service provider” guidance is the wrong analytical framework.119 As described, the protocol is an “anonymizing software provider” because it allows “a person that utilizes the software to anonymize the person’s own transactions.”120 And as noted, there are ways that an entity could interact with the protocol that arguably would make the entity a “money transmitter,” but the fact that users can anonymize their own transactions does not render the protocol a money transmitter on its own.121 The CVC Wallet test for intermediaries thus is the proper way to assess whether any component of Tornado Cash meets the definition of “money transmitting” under Section 1960(b)(2).
3. Applying the CVC Wallet Framework, No Component of Tornado Cash is a Money Transmitter.
Applying the CVC Wallet section from the 2019 Guidance, it is clear that no component of Tornado Cash is a money transmitter. The government misapplies the 2019 Guidance and fundamentally misunderstands the underlying technology involved in Tornado Cash. For example, the DOJ alleges “that the customers interact with the Tornado Cash service rather than with the Ethereum blockchain directly, [which weighs] in favor of a finding that the Tornado Cash service is a money transmitter.”122 This statement is factually incorrect and led the DOJ to wrongfully allege that the four-factor test weighs towards finding that Tornado Cash was a money transmitter.
We start with the Tornado Cash user interface (“UI”) component. Although it is true that the Tornado Cash developers created a UI to allow non-technical users to engage with the protocol, this is no different than unhosted wallet providers that definitively are not engaged in money transmission based on the 2019 Guidance and also “act as intermediaries between” the owner of CVC and the CVC itself.123 DOJ incorrectly posits that “[w]hile a customer with sophisticated technical ability could in theory generate a unique secret note that complied with the Tornado Cash service’s protocols, the Tornado Cash founders designed the user interface (‘UI’) so that it performed this function for any customer, and in practice the vast majority of customer deposits were made through the UI.”124 According to the government, the existence of the UI avoids any need to engage with the technical design of the protocol because the user is not generating their own cryptographic proofs. But that is inaccurate based on how the UI works.
When the user locks tokens, they generate the secret note locally on their device, with the help of the UI or not. At time tokens are locked, the transaction cannot happen without the user’s wallet providing (1) a valid signature corresponding to the exact denomination they wish to unlock, and (2) the commitment derived from the secret note they just stored locally on their device. Upon unlocking, the Tornado Cash UI cannot, and has never had the ability to, provide the zero-knowledge proof and nullifier needed to get the tokens on behalf of any user, since they do not have access to the secret note on the user’s device, which is needed to generate such values.
This is remarkably similar to self-hosted wallet software available to users. The secret note is no different than the user’s private keys, and just as is the case for self-hosted wallet software, the Tornado Cash UI simply provides a seamless interface to a user to get a technical product. Regardless of the existence of the UI, there is a need to engage with the technical operation of the protocol to conduct the Four-Factor Test from the FinCEN 2019 Guidance CVC Wallet Section.
Below we show that no component of Tornado Cash is a money transmitter based on that test:
i. Who Owns the Value?
At no time does any part of the protocol or the Tornado Cash UI ever “own” the value or hold the value in a custodial fashion for the user. As stated above, any ability to unlock tokens from the smart contracts requires that the user provide a valid proof and value (nullifier), neither of which can be generated without the secret note the user has stored locally on their device. Both are generated cryptographically based on the secret note, which neither the protocol nor the Tornado Cash UI can do on behalf of the user.
ii. Where is the Value Stored?
The DOJ alleges that this prong weighs towards a finding that Tornado Cash was engaged in money transmission. They posit that because “the ‘value’ in the Tornado Cash service is stored not with the customer but within the Tornado Cash pools” that Tornado Cash must be engaged in money transmission.126 This is incorrect.
The Tornado Cash developers never had the ability to access a user’s tokens or to generate a user’s secret key. The Tornado Cash smart contracts were not upgradeable after June 2020, meaning that the Tornado Cash developers could not change them if they wanted to nor can anyone now. There is no difference between holding funds in the Tornado Cash pools or holding them in a smart contract wallet, something that the DOJ should agree is covered under the CVC Wallet section.
The DOJ’s argument is predicated on the idea that simply because the Tornado Cash developers published the smart contract and that is where the value sits, then this prong must make the activity money transmission. But, if that were the case, there would be no need for the test because every single smart contract developer would be engaged in money transmission. It is impractical to believe that FinCEN meant for this prong of the analysis to be satisfied for every developer that publishes a smart contract. It must be the case that the question of where the value is stored is again a question of who controls the smart contract or wallet, and not simply asking who published the code.
This prong also incorporates the idea of control—who owns the wallet where the value is stored is discussed by FinCEN in the Guidance.127 And as previously stated, the Tornado Cash developers clearly do not have control and therefore this prong weighs against an overall finding that the protocol or its developers are money transmitters. Unlocking from the Tornado Cash smart contracts required two key user-generated values: cryptographic zero-knowledge proof, proving knowledge of the secret note without revealing it, and a valid generated value based on the secret note from the user which acts as the nullifier (which prevents double-spending). That is, was, and always will be the only way to unlock tokens from the protocol. No component of Tornado Cash or its developers ever held these key values on behalf of users.
The smart contracts on the Ethereum blockchain do not give the Tornado Cash developers ownership over the value that sits within that smart contract. That ownership remains with the user at all times, and therefore this prong should weigh against finding that the protocol or its developers are engaged in money transmission.The mechanics of how a smart contract works are critical to determining whether regulatory obligations may apply. In this case, with a smart contract that is non-upgradeable and non-custodial, we can see that the smart contract is functioning as a self-custodial wallet under the 2019 Guidance.
iii. Does the Owner Interact Directly With the Payment System Where the CVC Runs?
The DOJ alleges that users of the Tornado Cash protocol “interact with the Tornado Cash service rather than with the Ethereum blockchain directly.”128 That is wrong. The DOJ seems to be alleging that, because Tornado Cash provides its users with a seamless user interface that facilitates access to Ethereum, it is a money transmitter because, if accessed through a UI, the user does not directly interact with the Ethereum blockchain. If true, this position would, of course, make all providers of unhosted wallets money transmitters. The DOJ’s position on this point tells market participants that the best thing to do with the 2019 Guidance is tear it up and light it on fire. CVC Wallet providers offer a seamless key management experience to users so that a user can retain control of their tokens, store their private keys, and sign transactions in a self-custodial fashion without needing to be technical enough to generate their own private keys. Under the DOJ’s argument, anyone that facilitates use of Ethereum without the user writing their own Solidity code is engaged in money transmission.
As previously stated, the existence of the user interface does not change the underlying technical truth—that the user must provide cryptographic proofs that are only possible via access to the secret note to unlock their tokens. This act is not an act that happens within the non-existent “Tornado Cash Service.” These are immutable actions that provably happen on the Ethereum blockchain. Whether or not a user engages with Ethereum through a user interface or directly through code they write themselves has absolutely no bearing on whether they interact directly with the underlying blockchain. This prong of the test is clearly meant to delineate between fully off-chain services like a custodial exchange, where transactions often happen on the exchange’s own books, and a self-custodial product like a Metamask wallet or like the Tornado Cash protocol.
iv. Did Tornado Cash Ever Have Total Independent Control Over the User’s Funds?
The Tornado Cash protocol is a provably non-custodial set of smart contracts and at no time did the Tornado Cash developers have total independent control over user funds. The DOJ does not, and could not, dispute this point.129 The only way the Tornado Cash developers would be able to have independent control over a user’s tokens is if they could either upgrade the smart contracts, generate the secret note, or unlock tokens without generating a proof derived from the secret note. But nothing in the smart contracts130 or the UI holds such functionalities.
C. The DOJ Interpretation of Section 1960 Dramatically Expands the Scope of the Word “Transfer”
FinCEN was far more careful in crafting the 2019 Guidance than the DOJ has been in its allegations related to Tornado Cash. There already are a wide range of secondary effects in both the digital asset markets and in traditional financial markets due to the DOJ’s sweeping interpretation of “money transmitting.” And as others have properly noted, the DOJ’s interpretation of the word “transfer” is inconsistent with the statutory text.131
By arguing for a definition of money transmitting that is as broad as any person that causes funds to move between parties or locations, the DOJ seems to be supporting an expansion of the scope of money transmission regulation. This would invite absurd results.132 For example, numerous entities in the traditional financial services markets participate in payment card processing by communicating instructions that cause funds to be transferred, but they are not generally considered money transmitters.133 This includes entities that would not meet the specific “payment processor” exemption, including issuing payment processors, certain payment facilitators, and gateways, among others.134 A payment gateway is the interface a company uses to collect payment information and transmit that information to the financial institutions and processors involved in the transaction.135 A payment facilitator acts as a partner to handle a number of these back-end interactions to make this easier for merchants, especially smaller merchants.136 The activity of payment gateways and facilitators is often not money transmission and are a critical component of modern digital payments stack that move trillions of dollars of value seamlessly. The government’s position in Tornado Cash was not carefully considered, and, if affirmed in court, it could put significant portions of key payments markets at risk.
This definition could also be interpreted to cover the vast majority of blockchain infrastructure and Decentralized Finance (“DeFi”) market participants and further undermine the 2019 Guidance. Some examples of risks include:
CVC Wallet Providers;
Unhosted wallet providers are not considered to be engaged in money transmission based on the 2019 Guidance and the Four-Factor Test outlined above. If the DOJ’s position were to stand, the government could clearly argue that software that allows key management and transaction broadcasting of data to users of unhosted wallets is the “transferring” of funds, and allege that unhosted wallets are also engaged in regulated activity. This, of course, would directly contradict what is laid out in the 2019 Guidance.
Decentralized exchanges;
There is a carveout for decentralized exchanges in the 2019 Guidance, although, under the DOJ interpretation, a decentralized exchange may be engaging in the transfer of funds.
Similarly to Tornado Cash, a decentralized exchange (“DEX”) typically provides:
An underlying smart contract where assets are commingled to facilitate the movement of funds;
A website;
A retail-facing interface; and
Relayers to expedite these transactions.
Relayers
While the Tornado Cash allegations do not specifically allege that relaying alone would be considered money transmission, one could broadly read the “transferring of funds” interpretation to include solely providing relaying services. When relying on a relayer, the effect of accessing the service for the user is expediting the transfer of funds from one location to another.137
Validators.
Validators verify incoming transactions to a blockchain and access the historical record. Validators are necessary for the operation of blockchains and transfer of tokens to occur onchain. As such, we could imagine a dystopian reality where the government expands its interpretation of “transferring funds on behalf of the public by any and all means” to include validation services which, at their core, are solely a proof of the validity of underlying transaction data.
Such a broad interpretation could, with a stroke of a prosecutor’s pen, wrongly require market participants in huge swathes of the traditional and onchain financial markets, as well as non-financial markets (e.g., internet service providers, telephone carriers), to collect massive amounts of highly sensitive personal data for KYC to comply with the BSA. If applied as alleged, Section 1960 would be untethered from its statutory text and nearly the entire 2019 Guidance would be invalidated, undermining the careful balance Congress struck and the reasoned positions taken by FinCEN to facilitate compliance with the law. These obligations would also be unworkable and would cripple the development and ongoing operation of financial communications-related infrastructure activities within the United States.
The absurdity of this outcome could theoretically go well beyond just software that facilitates the movement of value by others. If this broad interpretation of Section 1960 is adopted and the law is not read to require control, any software that has any involvement with the value chain could be alleged to be money transmitter. This could implicate cloud computing services that underpin the entire American financial sector, technical hardware providers that provide the devices facilitating access to the internet and, therefore, to the movement of value, and technical security providers that ensure onchain and off-chain software is robust and make our technology and financial services ecosystem safer. If the government is interested in regulating all software that is associated with the value chain like we regulate financial institutions, then that choice should be made by the elected representatives of the American people, not prosecutors and judges. The U.S. government should not (again) force the U.S. Supreme Court to step in and protect Americans from extraordinary prosecutorial overreach in the application of criminal law.
Footnotes
The purpose of this paper is to point out the overbroad and potentially damaging position that the U.S. Department of Justice (“DOJ”) has taken with regard to its interpretation of unlicensed money transmission under 18 U.S.C. § 1960. We do not address any of the other counts of the indictment such as any violations of U.S. sanctions laws.
This paper benefitted greatly from thoughtful review and feedback from Michael Mosier, Jane Khodarkovsky, Clay Porter, Kenneth Blanco, Amanda Tuminelli, Gordon Liao, and Mira Belenkiy. Thank you to Isabel Yin for the excellent research assistance.
Tornado Cash Founders Charged With Money Laundering And Sanctions Violations, United States Attorney for the Southern District of New York (August 2023), https://www.justice.gov/usao-DOJ/pr/tornado-cash-founders-charged-money-laundering-and-sanctions-violations.
E.g., U.S. v. Sterlingov, 573 F. Supp. 3d 28 (D.D.C. 2021) (the prosecution of Bitcoin Fog, a cryptocurrency mixer, for operating an unlicensed money transmitting business); Sealed Superseding Indictment, United States v. Rodriguez (1:24-cr-00082), https://www.justice.gov/usao-DOJ/media/1349321/dl (indictment of the co-founders of Samourai Wallet, a mobile Bitcoin wallet that also operated a mixing service, Whirlpool); United States v. E-Gold, Ltd., 550 F. Supp. 2d 82 (D.D.C. 2008).
S. Rep. No. 101-460 (Sept. 12, 1990) (discussing money laundering enforcement exclusively with reference to drug money: “In the past, drug money laundering deterrence legislation has focused on depository institutions. However, as deterrence and compliance programs by depository institutions have improved, money launderers with illicit profits have found new avenues of entry into the financial system.”); see also H.R. Rep. 107-250(I) (Oct. 17, 2001) (maintaining discussion of drug money laundering and adding a reference to terrorism as part of discussing the PATRIOT Act amendments to Section 1960).
E.g., United States v. Faiella, 39 F. Supp. 3d 544, 545-46 (S.D.N.Y. 2014) (holding that Bitcoin “qualifies as ‘money’ or ‘funds’”). As our citation to a district court decision shows, there is little-to-no binding precedent defining “funds” under Section 1960. That said, initial research shows very few cases involving Section 1960 within the first 12 years of adoption, and all those cases involved the transmission of US
18 U.S.C. § 1960(b)(2). The indictment in United States v. Storm, No 1:23-cr-00430 (S.D.N.Y. Aug. 21, 2023), charges the defendant with violating 18 U.S.C. §§ 1960(b)(1)(B) and (b)(1)(C), but those charges are only available if Tornado Cash falls under § 1960(b)(2).
Fischer v. United States, 144 S. Ct. 2176, 2189 (2024) (cleaned up).
The guidance is often cited in various administrative rulings, which have precedential value. See, e.g., Request for Administrative Ruling on the Application of FinCEN’s Regulations to a Virtual Currency Trading Platform, FIN-2014-R011 (Oct. 27, 2014), https://www.fincen.gov/resources/statutes-regulations/administrative-rulings/request-administrative-ruling-application-0; see also 31 C.F.R. § 1010.715.
FinCEN, FinCEN’s Legal Authorities, available at https://www.fincen.gov/resources/fincens-legal-authorities#:~:text=31%20U.S.C.&text=This%20statute%20establishes%20FinCEN%20as,range%20of%20financial%20transactions%20information.
FinCEN, Mission, available at https://fincen.gov/about/mission.
FinCEN, Resources, available at https://fincen.gov/resources.
Blockchain analytics is one way to encourage proactive risk reduction without broadening the scope of money-services-business laws and forcing new actors, with no business interest in user data, to take possession of people’s sensitive and valuable personal information. The significant harms associated with data breaches are well known, and regulators should be working to embrace new technologies that reduce data proliferation, rather than forcing even more disclosure by users to even more entities and subjecting innocent users to these significant risks. E.g., Daniel J. Solove, Danielle Keats Citron, Risk & Anxiety: A Theory of Data-Breach Harms, 96 Tex. L. Rev. 737 (2018).
See FinCEN, FIN-2019-G001 Application of FinCEN’s Regulations to Certain Business Models Involving Convertible Virtual Currencies (May 9, 2019) 20, available at https://tinyurl.com/245626v5 (hereinafter the “2019 Guidance”), see also FinCEN, FIN-2013-G001 Application of FinCEN’s Regulations to Persons Administering, Exchanging, or Using Virtual Currencies (March 18, 2013), available at https://www.fincen.gov/statutes_regs/guidance/pdf/FIN-2013-G001.pdf (hereinafter the “2013 Guidance).
Our argument below describes why we believe that the DOJ is wrong with its recent interpretation of Section 1960. This argument is not meant to indicate that we do not believe FinCEN should have the tools in its toolkit to fight illicit finance and support the nation’s interest in countering money-laundering and terrorist financing. Rather, it is critical that we support that mission by respecting the work of FinCEN in crafting guidance for industry and consider how technical innovation can be leveraged by FinCEN to improve outcomes and reduce the amount of illicit financing in our financial markets. We do not believe that the DOJ’s broad interpretation of a criminal statute makes FinCEN’s mission more likely to succeed. In fact, it likely has the opposite effect by arguably capturing any software provider that is involved in the movement of value under FinCEN’s jurisdiction. By leveraging blockchain native tools, FinCEN can be embedded directly into the movement of value to achieve its goals, instead of forcing the responsibilities of a market participant that is engaged in financial intermediation onto software providers that are not engaged in that activity. We believe that regulators will be able to both catch bad actors and achieve their critical mission, while also protecting the data and financial privacy of Americans.
We are intentionally describing the process of interacting with the Tornado Cash protocol in terms that differ from the code in the smart contracts themselves. Although the code references below and the Fifth Circuit opinion in Van Loon use “deposit” and “withdrawal,” these terms are misnomers with legal and policy significance.
ERC-20 tokens are enabled by smart contracts and have a wide range of potential uses with other products and services. These tokens can be transferred and represent “an asset, right, ownership, access, cryptocurrency, or anything else that is not unique in and of itself.” Nathan Reiff, What Are ERC-20 Tokens on the Ethereum Network?, Investopedia (May 2024).
A nullifier is a cryptographic component used to ensure that a user cannot double-spend their assets when unlocking tokens from the Tornado Cash smart contract. When a user locks tokens into the Tornado Cash smart contract, they generate a secret note for a cryptographic commitment. This commitment is then recorded in the smart contract's Merkle tree. When the user wishes to unlock their tokens, they must provide a valid proof, which typically includes: (1) the cryptographic proof that they possess the secret corresponding to their locked tokens, and (2) the associated nullifier. This nullifier is derived from the locking and is unique to this transaction.
A commitment is the cryptographic equivalent of a padlock that can only be opened with the right secret - in this case, the owner's secret note.
During locking, the user creates a commitment to the secret note and secret nullifier. To unlock the token, the user presents a hash of the secret nullifier - the public nullification value. The cryptographic proof shows that the user knows the correct secret note for the padlock and that the hashed nullifier matches the committed nullifier. The smart contract stores the public nullification value for later. Anyone else trying to unlock the same token will end up presenting the same public nullification value because the hash of the secret nullifier is a deterministic function.
A Merkle tree is a cryptographic data structure used to efficiently and securely verify the integrity of large sets of data. Think of it as a hierarchical tree where:
Leaf Nodes: Each leaf node represents a single piece of data (e.g., a transaction or a commitment in Tornado Cash).
Non-Leaf Nodes: Each non-leaf node is a cryptographic hash of its immediate child nodes.
In Tornado Cash, the Merkle tree stores all the commitments (unique cryptographic proofs of token locks). When a user wants to unlock tokens, they provide a Merkle proof that their commitment exists in the tree without revealing which specific commitment it is. This ensures:
Privacy: The link between the token lock and unlock remains hidden.
The Merkle tree stores only the list of commitments - padlocks - but not the owners of the commitments. The contract uses Merkle tree data structure for storage.
See supra note 21.
Early in the protocol’s history, there were certain functions that allowed changes to aspects like the verifier address, but no functions ever existed that would have allowed the protocol to control a user’s tokens. These early functions were removed in 2020 as part of the “trust setup ceremony.” See Van Loon v. Dep’t of the Treasury, No. 23-50669, 2024 WL 4891474, at *4 (5th Cir. Nov. 26, 2024).
2024 WL 4891474, at *1.
Id. at *4.
Id. at *3.
Id. (emphasis added).
Id. at *9.
Id. at *11.
Id. at *12.
Id. The Court expressly distinguished vending machines, which have “an owner—or counter-party—who can exercise some control over it.” Id.
See OpenPGP, History, available at https://www.openpgp.org/about/history/.
NBC News, U.S. officials urge Americans to use encrypted apps amid unprecedented cyberattack (Dec, 3, 2024) (Quoting Jeff Greene, Jeff Greene, executive assistant director for cybersecurity at the Cybersecurity and Infrastructure Security Agency, as saying “Our suggestion, what we have told folks internally, is not new here: Encryption is your friend, whether it’s on text messaging or if you have the capacity to use encrypted voice communication. Even if the adversary is able to intercept the data, if it is encrypted, it will make it impossible.”)
See Van Loon, 2024 WL 4891474, at 34 (“Mending a statute’s blind spots or smoothing its disruptive effects falls outside our lane. We decline the Department’s invitation to judicial lawmaking—revising Congress’s handiwork under the guise of interpreting it. Legislating is Congress’s job—and Congress’s alone”).
Id. at *14 (noting that “IEEPA became law in 1977, years before the modern Internet was even invented”).
Dubin v. United States, 599 U.S. 110, 129 (2023); accord Snyder v. United States, 144 S. Ct. 1947, 1960 (2024) (Gorsuch, J., concurring) (“[A]ny fair reader of this statute would be left with a reasonable doubt about whether it covers the defendant’s charged conduct. And when that happens, judges are bound by the ancient rule of lenity to decide the case as the Court does today, not for the prosecutor but for the presumptively free individual.”).
144 S. Ct. 1947 (2024).
599 U.S. 110 (2023).
584 U.S. 1 (2018).
579 U.S. 550 (2016).
Dubin, 599 U.S. at 129; accord Fischer, 144 S. Ct. at 2189 (“novel interpretation would criminalize a broader swath of prosaic conduct”); Snyder, 144 S. Ct. at 1959 (“interpretation of [the statute] that would radically upend gratuities rules and turn [the statute] into a vague and unfair trap for 19 million state and local officials”); Marinello, 584 U.S. at 9 (“[a] broad interpretation would also risk the lack of fair warning and related kinds of unfairness”); McDonnell, 579 U.S. 550 at 580 (2016) (“the Government’s boundless interpretation”); see also Van Buren v. United States, 141 S. Ct. 1648, 1661 (2021) (“criminalize everything from embellishing an online-dating profile to using a pseudonym on Facebook”).
144 S. Ct. at 2181 (noting that (c)(1) provides: “anyone who corruptly ‘alters, destroys, mutilates, or conceals a record, document, or other object, or attempts to do so, with the intent to impair the object’s integrity or availability for use in an official proceeding’”; and (c)(2) provides: “otherwise obstructs, influences, or impedes any official proceeding, or attempts to do so”).
Id. at 2183.
Id. at 2189.
Id. (cleaned up).
144 S. Ct. at 1951.
Id. at 1957 (discussing option (a), the Court noted that “that draconian approach would border on the absurd and exacerbate the already serious federalism problems with the Government’s reading of” the statute).
Id.
Id. at 1958.
599 U.S. at 113-15.
Id. at 116-17.
Id. at 129-30.
Id. at 130 (citation omitted; cleaned up).
593 U.S. at 378.
Id. at 379-80.
Id. at 389.
Id. at 393.
584 U.S. at 4 (cleaned up).
Id. at 4, 7-10.
Id. at 11.
McDonnell, 579 U.S. at 566.
Id. at 567.
Id. at 576 (cleaned up).
Dubin, 599 U.S. at 131.
McDonnell, 579 U.S. at 576; accord Snyder, 144 S. Ct. at 1958; Dubin, 599 U.S. at 131; Marinello, 584 U.S. at 11.
Dubin, 599 U.S. at 131.
18 U.S.C. § 1960(a).
E.g., Snyder, 144 S. Ct. at 1954.
Black’s Law Dictionary (12th ed. 2024). All definitions provided are from this version of Black’s Law Dictionary.
All citations are to Merriam Webster online at: https://www.merriam-webster.com/ for the sake of availability. Where possible, parallel citations are provided to an electronically available print dictionary that is contemporaneous with Section 1960’s enactment to demonstrate consistent meaning over time.
“Fund,” Merriam Webster, https://www.merriam-webster.com/dictionary/fund (last visited Oct. 21, 2024); accord “Fund,” The American Heritage Dictionary of the English Language (3d ed. 1992) (“A sum of money or other resources set aside for a specific purpose . . . .”).
“Electronic funds transfer,” Merriam Webster, https://www.merriam-webster.com/dictionary/electronic%20funds%20transfer (last visited Oct. 21, 2024).
See supra note 5.
“Wire Transfer,” Merriam Webster, https://www.merriam-webster.com/dictionary/wire%20transfer (last visited Oct. 21, 2024); accord “Wire,” American Heritage Dictionary, supra note 72 (“5. To send by telegraph.”).
Black’s Law Dictionary (12th ed. 2024).
“Check,” Merriam Webster, https://www.merriam-webster.com/dictionary/check (last visited Oct. 21, 2024); accord “Check,” American Heritage Dictionary, supra note 72 (“A written order to a bank to pay the amount specified from funds on deposit; a draft.”).
Black’s Law Dictionary (12th ed. 2024).
“Draft,” Merriam Webster, https://www.merriam-webster.com/dictionary/draft (last visited Oct. 21, 2024); accord “Draft,” American Heritage Dictionary, supra note 72 (“A written order directing the payment of money from an account or fund.”).
Black’s Law Dictionary (12th ed. 2024).
“Facsimile,” Merriam Webster, https://www.merriam-webster.com/dictionary/facsimile (last visited Oct. 21, 2024); accord “Facsimile,” American Heritage Dictionary, supra note 72 (“A method of transmitting images or printed matter by electronic means.”).
Black’s Law Dictionary (12th ed. 2024).
“Courier,” Merriam Webster, https://www.merriam-webster.com/dictionary/courier (last visited Oct. 21, 2024); id., “Messenger,” https://www.merriam-webster.com/dictionary/messenger (last visited Oct. 21, 2024); accord “Courier,” American Heritage Dictionary, supra note 72 (“A messenger, especially one on official diplomatic business.”); id., “Messenger” (“One that carries messages or performs errands, as a: A person employed to carry telegrams, letters, or parcels.”).
18 U.S.C. § 1960(b)(1)(B).
31 U.S.C. § 5330(a)(1).
Id.; see also 1 U.S.C. § 1 (defining “person” to “include corporations, companies, associations, firms, partnerships, societies, and joint stock companies, as well as individuals”). A more detailed assessment of “business” under Section 1960 was recently published and further expands on the critical role this term plays in the statutory analysis. Daniel Barabander, Amanda Tuminelli, Jake Chervinsky, Through the Looking Glass: Conceptualizing Control & Analyzing Criminal Liability for Unlicensed Money Transmitting Businesses Under Section 1960 at 26-31, Int’l Academy of Fin. Crime Litigs (Dec. 2024), https://edit.financialcrimelitigators.org/api/assets/cd682a1c-1cb0-4c99-a491-ac6155f4bdc2.pdf.
31 U.S.C. § 5330(d).
Van Loon, 2024 WL 4891474, at *21.
Compare Pub. L. 102-550, 106 Stat. 4057 (Oct. 28, 1992) (enacting Section 1960), with Pub. L. 103-325, 108 Stat. 2250 (Sept. 23, 1994) (enacting Section 5330). Section 1960 was later amended through the PATRIOT Act, but the amendment did not change the text of § 1960(b)(2). See Uniting and Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism (USA PATRIOT Act) Act of 2001, Pub. L. No. 107-56, § 361, 115 Stat. 272, 329 (2001); accord Barabander, Tuminelli, Chervinsky, Through the Looking Glass, supra note 86, at 11.
“Statutory Interpretation: Theories, Tools, and Trends,” Congressional Research Service, at 58 (Apr. 5, 2018) (citation omitted), https://crsreports.congress.gov/product/pdf/R/R45153/2.
18 U.S.C. § 1960(b)(1); 31 U.S.C. § 5330(d)(1).
18 U.S.C. § 1960(b)(2); 31 U.S.C. § 5330(d)(2).
18 U.S.C. § 1960(b)(1)(C), (b)(2); 31 U.S.C. § 5330(d)(1)-(2).
United States v. Freeman, 44 U.S. 556, 564 (1845); Statutory Interpretation: Theories, Tools, and Trends, supra note 90, at 61 (“when similar statutory provisions are found in comparable statutory schemes, interpreters should presumptively apply them the same way” (citation omitted)); see also id. at 56 (“Noscitur a Sociis: ‘Associated words bear on one another’s meaning’” (citation omitted)); id. at 58 (“Presumption of Consistent Usage: ‘Generally, identical words used in different parts of the same statute are . . . presumed to have the same meaning.’” (citation omitted)).
Smith v. City of Jackson, 544 U.S. 228, 233 (2005) (“[W]hen Congress uses the same language in two statutes having similar purposes, particularly when one is enacted shortly after the other, it is appropriate to presume that Congress intended that text to have the same meaning in both statutes.”); see also Voisine v. United States, 579 U.S. 686, 702 (2016) (noting that “the same words in a statute presumptively have the same meaning”). To the extent there are textual differences between the statutes—Section 5330 adds “currency” and “value that substitutes for currency”—the additional categories listed in Section 5330 must be read as expanding the transactions covered by Section 5330 to avoid surplusage. Id. at 59 (“Rule Against Surplusage: Courts should ‘give effect, if possible, to every clause and word of a statute’ so that ‘no clause is rendered superfluous, void, or insignificant.’” (citations omitted)). The Court in Storm rejected that “the definitions of ‘money transmitting’ in Sections 1960 and 5330 are co-extensive,” but provided no analysis. Transcript, United States v. Storm, No. 23-cr-430, at 20 (Sept. 26, 2024). The Court’s bare assertion is inconsistent with the statutory interpretation approach articulated by the U.S. Supreme Court. E.g., Smith, 544 U.S. at 233.
Antonin Scalia & Bryan A. Garner, Reading Law: The Interpretation of Legal Texts, at 180 (2012).
FDA v. Brown & Williamson Tobacco Corp., 529 U.S. 120, 133 (2000) (“fit, if possible, all parts into a harmonious whole”) (citations omitted). Cf. Gustafson v. Alloyd Co., Inc., 513 U.S. 561, 570 (1995) (“[W]e adhered to the ‘normal rule of statutory construction’ that ‘identical words used in different parts of the same act are intended to have the same meaning.’”) (citation omitted). Indeed, Section 1960(b)(1)(B) expressly refers to Section 5330, so reading them consistently is what Congress would have reasonably anticipated.
FTC v. Wyndham Worldwide Corp., 799 F.3d 236, 249, 251 (3d Cir. 2015) (emphasizing that “even in the civil context, fair warning requires that government agencies communicate their interpretation of their own regulations with "ascertainable certainty" before subjecting private parties to punishment under that interpretation); accord United States v. Harra, 985 F.3d 196, 213 (3rd Cir. 2021) (the court noted that if a regulator fails to give fair warning, it may still succeed in a false statement prosecution—but only if it proves either that its interpretation is the only reasonable one or that the defendant's statement is false under each reasonable interpretation”); see also United States v. Richter, 796 F.3d 1173, 1190 (10th Cir. 2015) (noting that “actual notice of an agency's interpretation—even an interpretation that lacks the force and effect of law—can meet the demands of fair notice.”). This suggests that even without having the force of law, agency interpretation can be relevant to a court's determination of whether prosecution is warranted on due process grounds.
2013 Guidance, 2019 Guidance.
Prepared Remarks of FinCEN Director Kenneth A. Blanco, delivered at the 12th Annual Las Vegas Anti-Money Laundering Conference, FinCEN (August 2019).
The government itself has previously cited to the 2019 Guidance in enforcement actions against defendants that were allegedly in violation of those obligations. See Harmon, 474 F. Supp. 3d at 106. It has also cited to the 2013 Guidance in enforcement actions. See Faiella, 39 F. Supp. 3d at 546.
The Government’s Opposition to Defendant Roman Storm’s Pretrial Motions at 33, U.S. v. Storm, 1:23-cr-00430, 23 Cr. 430 (KPF), (S.D.N.Y April 26, 2024) [hereinafter DOJ Motion].
See, e.g., Government’s Opposition to Defendant’s Motion to Dismiss Counts Two and Three at 17-18, U.S. v. Harmon, 474 F. Supp. 3d 76 (D.D.C. 2020) (arguing that “money transmitting businesses” in §5330 was intended to capture a “broad array” of financial transactions, including the HELIX mixer at issue, and that § 1010(ff)(5)(i)(B) was similarly a “catch-all” definition encompassing HELIX).
See id. at 19-22.
See Government’s Opposition to Defendant’s Motion to Dismiss the Indictment at 19, U.S. v. Sterlingov, 573 F. Supp. 3d 28 (D.D.C. 2021).
Harmon, 474 F. Supp. 3d at 108–09 (emphasis added).
2019 Guidance at 15.
Id. (emphasis added).
DOJ Motion at 32. Note that the government refers to “the Tornado Cash service,” but there is no such omnibus “service.” As reflected throughout this paper, Tornado Cash technically is made up of different components, and a user does not need to leverage every component in order to use the protocol.
2019 Guidance at 19-20.
Id.
Id. at 19 (emphasis added).
Id. at 19.
Id. at 20.
Id. at 2.
Id. at 19.
See 2019 Guidance. For the custodial mixer cases, see Sterlingov, 573 F. Supp. 3d 28 (supra note 4); see also U.S. Treasury Issues First-Ever Sanctions on a Virtual Currency Mixer, Targets DPRK Cyber Threats, U.S. Treasury (2022), https://home.treasury.gov/news/press-releases/jy0768 (discussing the OFAC sanction of Blender.io, a custodial mixing service).
See supra Part II.A.
2019 Guidance at 19.
Id. at 20
Id.
DOJ Motion at 33. As a reminder, the DOJ packages together different (and separate) components to allege that there is a “Tornado Cash service,” including the relayers. But these components are all separate, individually operating pieces of the puzzle, and it is not a homogenous “service” as DOJ asserts.
2019 Guidance at 15.
DOJ Motion at 9.
This is an image of the UI shown to a user when the user is about to lock tokens into the smart contracts. As shown in clear capitalized orange letters, it is the responsibility of the user to retain the “key” (secret note) to their own tokens; neither the protocol nor the UI has custody over the secret note or the tokens and cannot retrieve either the tokens or the secret note.
DOJ Motion at 32-33.
2019 Guidance at 16.
DOJ Motion at 33.
See, e.g., Benjamin Gruenstein, Evan Norris, Daniel Barabander, Secret Notes & Anonymous Coins: Examining FinCEN’s 2019 Guidance on Money Transmitters in the Context of the Tornado Cash Indictments at 15-16, Int’l Academy of Fin. Crime Litigs. (Sept. 2023), https://www.cravath.com/a/web/qyCBWVBLEMsqxPHtd9ykoc/87ntut/the-international-academy-of-financial-crime-litigators.pdf.
Contracts available here: Tornado-core/contracts, https://github.com/tornadocash/tornado-core/blob/master/contracts/Tornado.sol.
Barabander, Tuminelli, Chervinsky, Through the Looking Glass, supra note 86, at 12-25.
Statutory Interpretation: Theories, Tools, and Trends, supra note 90, at 43; see also Clinton v. City of New York, 524 U.S. 417, 429 (1998) (“Acceptance of the Government’s new-found reading of [the disputed statute] ‘would produce an absurd and unjust result which Congress could not have intended.’”) (quoting Griffin v. Oceanic Contractors, Inc., 458 U.S. 564, 574 (1982)).
See, e.g., What is a money transmitter? Definition and license requirements, Stripe (September 2024), (explaining the differences in transactions, services provided, and regulatory oversight for money transmitters vs. payment processors); see also Online Payment Systems - Are You a Payment Processor or a Money Transmitter?, Moses Singer (Mar. 2024), available at https://www.mosessinger.com/banking-finance/publications/online-payment-systems-are-you-a-payment-processor-or-a-money-transmitter.
FinCEN stipulates four conditions for the payment processor exemption to apply to a particular business pattern: (1) the entity providing the service must facilitate the purchase of goods or services, or the payment of bills for goods or services (other than money transmission itself); (2) the entity must operate through clearance and settlement systems that admit only BSA-regulated financial institutions; (3) the entity must provide the service pursuant to a formal agreement; and (4) the entity’s agreement must be at a minimum with the seller or creditor that provided the goods or services and receives the funds. See Application of Money Services Business Regulations to a Company Acting as an Independent Sales Organization and Payment Processor, FinCEN (August 2014), https://www.fincen.gov/resources/statutes-regulations/administrative-rulings/application-money-services-business.
Payment Facilitator vs Payment Gateway: Key Differences and Similarities, Stax Payments, https://staxpayments.com/blog/payment-facilitator-vs-payment-gateway/.
Id.
We are not addressing the relayer registry for Tornado Cash as part of this paper.